
The licensed version of Spike.
We're bits and bytes programmers. Most at home in the bowels of an operating system. When first we considered venturing out from the subterranean and into the world of the Internet, we looked at what was already available there. And noticed a few things which, frankly, did not surprise us at all:
We looked at these applications, tried and tested every one, and always thought the same thing: at 350,000 bytes or 400,000 bytes, or even a million bytes, what is going on there? What is being done in all that code? Can anything justify such a bloated disk image, for any program, especially - for a Winsock utility?
We came to the conclusion that no, nothing could justify such an atrociously inflated image. Nothing. But we had yet to prove it.
Now, of course, we have.
Spike offers what most generic Winsock utilities do, even adding a function of its own, yet weighs in not at 800,000 bytes, nor 400,000, nor a mere 350,000 - but 15,872 (FIFTEEN THOUSAND EIGHT HUNDRED SEVENTY TWO) bytes. And Spike diverges from the general trend of using a standard property sheet for its implementation, and for a number of reasons:
So we used a tree view instead. And successfully, we would like to add. TUCOWS in particular has taken a real liking to Spike. As for the name, it comes from Goldeneye, Izabella Scorupco's famous command line: "SEND SPIKE". Initially we saw a further connotation in the name, ala Tom Petty's song, but our search for an icon with red and white beanie with a propeller on top was in vain, so we just stuck to the one we had.
Spike diverges in another respect from most Winsock utilities: it's written to integrate into your desktop and your work on the Internet. It fires up and disappears immediately to your system tray. Its appearance can be toggled at any time. It retains its data from appearance to appearance (very important). It does not require a lot of lugubrious copying and pasting from entry field to entry field to get the job done - all the Spike functions share the same fields.
Spike is multithreaded, meaning that while it's working for you, you can make it disappear or go on to some other function.
As far as we know, our Block, Ping, and Trace functions offer the most complete diagnostics found in any Winsock utility as well. We cover all return values, and turn each of these into an "intelligible" string, where most Winsock utilities will simply print "no response."
Most Winsock apps will display basic Winsock information, and this is no big deal, as it's available to any thread as soon as they initialize the sockets layer. It's just a question of reading back the data sent by the operating system. So we print it as well.
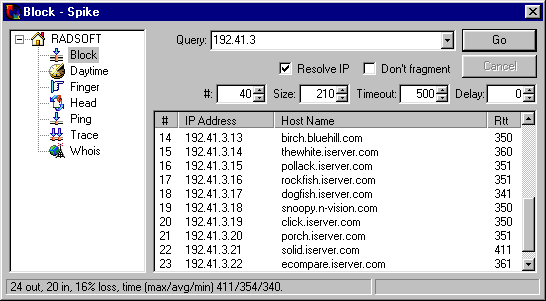
This is a new function, which frankly we've found very useful. Block starts at any URL, converts it to an IP if necessary, and then starts pinging away. It tells you what the "neighbors" of a specific URL are. All we can say is: "try it!" You'd be surprised what you can learn...
This is not a clock sync function, but a standard UNIX feature implemented by many Internet servers. They send back the time of day as a readable ASCII string, from their corner of the world, as they see it.
Takes an email address, or often just a host as well. Try putting the '@' in front of the server name if it doesn't work without. Availability of a finger service is dependent on the remote host. Some implement it, some do not, some implement, in our opinion, all too much, disclosing what we consider to be confidential information about the users on a particular network. Check your own email address and see what's being broadcast about you.
The classic ICMP function. Attempts to access a remote host and reports back with the address returned by that host. Also reports on the time taken to "bounce back" from that host. You can set the number of pings, the packet size, the ping timeout, and the delay between successive pings.
And, as stated above, our Block, Ping, and Trace functions offer the most complete diagnostics found in any Winsock utility anywhere. We cover all return values, and turn each of these into an "intelligible" string, where most Winsock utilities will simply print "no response."
Many Winsock applications will make the assumption that arriving at a destination is the main point of a ping, and put a number of access attempts into a loop, most often three. This is wrong, we cannot but categorically state this and move on. When you "loop" within a number of ping attempts, most often you never know if your remote host was accessible on the first attempt or not. Part of the idea with a ping is to find out not just if a remote host is accessible, but exactly how accessible it is.
Similar to Ping, but works in a cute and clever way (we didn't invent it, it's an old UNIX thing). Trace (or traceroute) traces a route - i.e. tells you the path used to access a remote host. It starts by only allowing the ping packet a single hop - so it finds the next destination and returns immediately with a "timed out" message. Which nevertheless establishes where your communications with that remote host will turn to first. The second packet is allowed two hops, the third three, etc. Finally - hopefully - you will arrive at your destination.
Contrary to Ping, Trace can benefit from multiple attempts to access a particular hop URL. The whole idea is to find out the path used to access a remote URL, not find out how reliable any hop along the way happens to be. Trace uses a loop whereby any access is attempted up to three times - which is a standard empirical value used in the world of UNIX and the net.
Finally, Trace really tells you if you arrive at your destination, whereas most Winsock utilities do not. They simply quiet down and die. If you do arrive, you might not actually recognize the URL reported back. Therefore Spike will print "Arrived" in his far right status window when you do in fact "arrive."
A particularly classic UNIX utility which is well implemented here. Whois tells you who someone is - given their URL, Whois, through the auspices of one of a number of whois servers, will tell you - yep - who that URL is.
A number of standard whois servers are provided by Spike automatically, and they should serve almost all generic searches:
Any Spike readout will allow copying to the clipboard for further use. You might want to paste the results of a query into a text editor, for example, for printing out. This also applies to Spike's list views as used by Block, Ping, and Trace. Try right clicking on the list view and see what happens.
Many popular Winsock utilities out there do some very bad coding as regards process and thread management within Win32, creating havoc in your RAM and address spaces. Spike, of course, does nothing of the sort.
Spike is one of 78 Win32 apps currently found in Rix2k Extreme Power Tools. Visit the Radsoft site for more information.
Disk image size: 19,968 bytes (licensed version).